Stay safe this summer! Get free cybersecurity awareness training and learn the top 2025 threats. Protect your data on vacation with our expert tips and checklist.
While you’re planning your vacation, cybercriminals are planning their attacks. Here’s how to stay one step ahead, for free, and ensure your summer memories are the only thing you bring back.
As the temperature rises and vacation plans solidify, the last thing on your mind is probably your digital security. You’re thinking about beach towels, not data breaches. But here’s a startling reality: the summer season is a goldmine for cybercriminals who prey on our relaxed, “out-of-office” mindset. An increased reliance on public Wi-Fi, last-minute travel bookings, and a general state of vacation bliss make us prime targets.
This is why bolstering your cybersecurity awareness is more critical than ever. As we look toward the summer of 2025, the threats are evolving, becoming smarter, and more personal. But the good news is, so are the defenses—and many of them are completely free.
This guide is your all-in-one resource for summer cybersecurity awareness 2025. We will unpack:
- The emerging cyber threats you need to watch out for this summer.
- A curated list of top-tier, FREE cybersecurity training resources to level up your skills.
- An actionable checklist to secure your devices and data before, during, and after your vacation.
- Expert answers to your most pressing cybersecurity questions.
Let’s dive in and make sure your summer is remembered for sunshine and relaxation, not scams and stress.
Why Summer is a Hacker’s Favorite Season
Cybercriminals don’t take vacations; they wait for you to take yours. The shift in our routines and environments during the summer months creates a perfect storm of vulnerabilities that hackers are eager to exploit.
- Increased Use of Public Wi-Fi: From airports and coffee shops to hotels and Airbnbs, we’re constantly connecting to unfamiliar networks. Unsecured public Wi-Fi is like leaving your front door wide open, allowing criminals on the same network to intercept your data.
- The Relaxation Factor: When we’re mentally checked out, our guard is down. We’re more likely to click on a suspicious “flight delay” text or a “special offer” email without the critical scrutiny we might normally apply at our work desk.
- Physical Distance from Support: When you’re thousands of miles from home or the office IT department, resolving a security issue becomes significantly more challenging. Criminals count on this delay to maximize their damage.
- Remote Work Blurring Boundaries: The “workcation” trend means sensitive company data is often accessed from less secure personal laptops and networks in vacation rentals, compounding the risk.
Emerging Summer Cybersecurity Awareness Trends for 2025
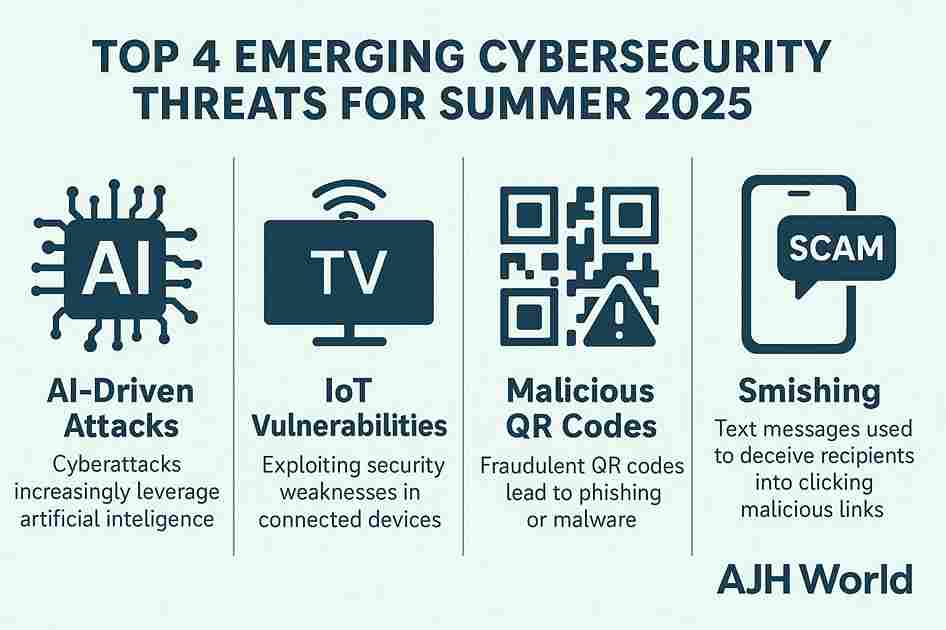
To stay ahead, you need to know what’s coming. Standard phishing emails are old news. For summer cybersecurity awareness 2025, be prepared for these sophisticated threats.
Hyper-Personalized AI Phishing Scams
Forget the poorly worded emails of the past. Generative AI now allows criminals to create highly convincing and personalized phishing emails, texts (smishing), and even voice messages (vishing).
- What to Watch For: Imagine an email that references your recent hotel booking by name, mentioning the local area and offering a “complimentary upgrade.” Or a text about a “package delivery issue” for that swimsuit you just ordered. The level of detail makes these scams incredibly difficult to spot.
- How to Act: Always verify through official channels. Don’t click the link in the email. Go directly to the airline’s or hotel’s website or app to check your reservation status.
Travel and Hospitality IoT Vulnerabilities
The Internet of Things (IoT) is everywhere—from the smart lock on your rental to the hotel’s smart TV. While convenient, these devices are often a weak link in the security chain.
- What to Watch For: A compromised smart TV could potentially have a hidden camera or keylogger to steal passwords you type into its apps (like Netflix or YouTube). A poorly secured smart home hub in a rental could expose the Wi-Fi network you’re using.
- How to Act: Avoid logging into sensitive accounts on public or shared devices. When connecting to rental Wi-Fi, use a trusted VPN to encrypt all your traffic. For a deeper dive, check out our guide on What is a VPN and Why You Need One.
H3: The Rise of QR Code & “Smishing” Attacks
QR codes are on every restaurant menu and promotional poster. This convenience has been weaponized by attackers in a tactic called “quashing” (QR code phishing).
- What to Watch For: A malicious QR code could be a sticker placed over a legitimate one, leading you to a fake payment portal or a site that downloads malware onto your phone. Smishing (SMS phishing) will be rampant with fake alerts about flight changes, rental car confirmations, or bank fraud.
- How to Act: Be cautious about which QR codes you scan. If it’s a sticker that looks out of place, avoid it. For texts, never click links. Log in directly to the service provider’s official website to verify any alert.
Public Wi-Fi and Juice Jacking 2.0
The danger of public charging stations—a threat known as “juice jacking,” where a compromised USB port can steal data or install malware—is evolving. The same risk applies to using unfamiliar charging cables left behind in hotels or cafes.
- How to Act: Never use a public USB charging port. Use your own AC power adapter and plug it into a traditional wall outlet. Carry a portable power bank as your primary charging source when traveling.
Your Ultimate Toolkit: The Best FREE Cybersecurity Training Resources
You don’t need an expensive course to dramatically improve your cybersecurity awareness. These incredible resources are used by professionals and are available to you for free.
- SANS Cyber Aces Online:Link to SANS.org
- What it is: SANS is one of the most respected names in cybersecurity training. Their Cyber Aces program provides free courses covering the foundational concepts of operating systems, networking, and system administration, which are the building blocks of security.
- Best for: Beginners and students who want a structured, in-depth introduction to core concepts.
- Fortinet’s Network Security Expert (NSE) Program:Link to Fortinet.com
- What it is: Fortinet has made its core NSE 1 and NSE 2 certification training completely free. These courses provide an excellent overview of the modern threat landscape and the fundamental strategies used to combat it.
- Best for: Anyone, from students to professionals in non-IT roles, who wants a comprehensive understanding of current cyber threats.
- Cybrary:Link to Cybrary.it
- What it is: Cybrary offers a huge catalog of free, open-source cybersecurity and IT training content. You can find introductory courses on everything from ethical hacking to network security.
- Best for: Self-starters who want to browse and sample a wide variety of topics at their own pace.
- Federal Trade Commission (FTC) – Cybersecurity for Small Business:Link to FTC.gov
- What it is: While aimed at small businesses, the principles and training materials offered by the FTC are universally applicable. It’s practical, non-technical, and focuses on real-world actions like preventing phishing and securing networks.
- Best for: Non-technical individuals, families, and freelancers who want straightforward, actionable advice.

The Actionable Summer Cybersecurity Checklist
Use this checklist to secure your digital life before, during, and after your trip.
Before You Go:
- Update Everything: Install all operating system, browser, and app updates. These often contain critical security patches.
- Back Up Your Data: Back up important files from your phone and laptop to a cloud service or an external hard drive.
- Install a VPN: Subscribe to and install a reputable VPN on all devices you’re bringing.
- Strengthen Passwords: Use a password manager and ensure all critical accounts (email, banking) have strong, unique passwords. Review our Bitcoin Price and Tariff Impact 2025: Why BTC Climbs Past $109K for help.
- Enable Multi-Factor Authentication (MFA): Turn on MFA for all important accounts. It’s your single best defense against stolen passwords.
- Inform Your Bank: Let your bank know about your travel plans to avoid legitimate purchases being flagged as fraud (and to help them spot actual fraud faster).
During Your Trip:
- Avoid Public Wi-Fi for Sensitive Tasks: Use your phone’s data hotspot or wait until you’re on a trusted network for banking or shopping.
- Always Use Your VPN: When you must use hotel or airport Wi-Fi, turn on your VPN first. It encrypts your data, making it unreadable to snoops.
- Disable Auto-Connect: Turn off Wi-Fi and Bluetooth auto-connect features to prevent your device from connecting to malicious networks without your permission.
- Charge Safely: Use an AC wall adapter or a portable power bank. Never plug your phone into a public USB port.
- Be Skeptical of All Unsolicited Messages: Treat every “urgent” text or email about your travel plans as a potential scam. Verify directly with the provider.
After You Get Home:
- Scan for Malware: Run a full antivirus/anti-malware scan on your devices.
- Monitor Your Accounts: Keep an eye on your bank and credit card statements for any unusual activity in the weeks following your trip.
Frequently Asked Questions (FAQs)
Phishing and smishing will be the biggest threat. Using AI, scams related to flight confirmations, hotel bookings, and vacation deals will be extremely personalized and difficult to distinguish from legitimate communications. Always verify information through official apps or websites, not through links in messages.
Yes, using a reputable VPN makes connecting to hotel or any public Wi-Fi significantly safer. The VPN creates an encrypted “tunnel” for your data, shielding it from anyone on the same network who might be trying to intercept it. Without a VPN, your activity can be easily monitored.
You can start today! A great first step is to explore the Fortinet NSE 1 and 2 courses or the introductory materials on Cybrary. These free resources are designed for beginners and provide a fantastic overview of the threat landscape and defensive principles.
The #1 tip is to cultivate a healthy sense of skepticism. Before you click any link, scan any QR code, or provide any information, take a five-second pause and ask, “Is this legitimate? Is there another way I can verify this?” This simple habit can prevent the vast majority of attacks.
Enable screen locks with a strong passcode or biometric ID on all devices. Turn on “Find My” features (like Find My iPhone or Find My Device for Android) to track, lock, or wipe your device if it’s lost or stolen. Also, be physically mindful of your devices in crowded public places.
Summer should be a time of rejuvenation, not regret. By understanding the evolving threat landscape and taking a few proactive steps, you can ensure your digital life is as secure as your home is while you’re away. The threats for summer 2025 are more sophisticated, but your awareness is your strongest shield.
Leverage the incredible free training resources available to you, follow the simple checklist, and adopt a mindset of healthy skepticism. Investing a small amount of time in your cybersecurity awareness today will pay huge dividends in protecting your finances, data, and peace of mind. Now you have the knowledge and tools for superior summer cybersecurity awareness 2025—go and enjoy your well-deserved break!
What is your #1 cybersecurity tip for staying safe during the summer? Share it in the comments below!
John Secord is a certified cybersecurity analyst with over 10 years of experience helping individuals and businesses stay safe in the digital world. He believes that strong security starts with clear, accessible education and is passionate about empowering everyone to protect their data.



Leave a Comment